In today’s digital landscape, where data breaches and cyber attacks have become increasingly prevalent, ensuring the security of web applications and APIs is critical. While most developers are familiar with the concept of authentication, a crucial aspect that often gets overlooked or misunderstood is authorization. We’ll explore a real-world scenario, identify common security risks, and discuss mitigation strategies. So let’s get started!
Authorization vs. Authentication: Clarifying the Terminology
Before we jump into the specifics, let’s clarify the difference between authorization and authentication. Authorization is the process of determining what resources or functionalities a user can access within an application. It revolves around identifying and granting appropriate permissions. On the other hand, authentication involves verifying the identity of a user and ensuring that they are who they claim to be. So it makes sense that you wouldn’t want to give someone access to things before you know who they are.
Unveiling Security Risks in Development Environments
Let’s examine a practical example to understand this better. Consider an e-commerce store built on a Ruby on Rails framework, a fork of the Spree e-commerce platform.
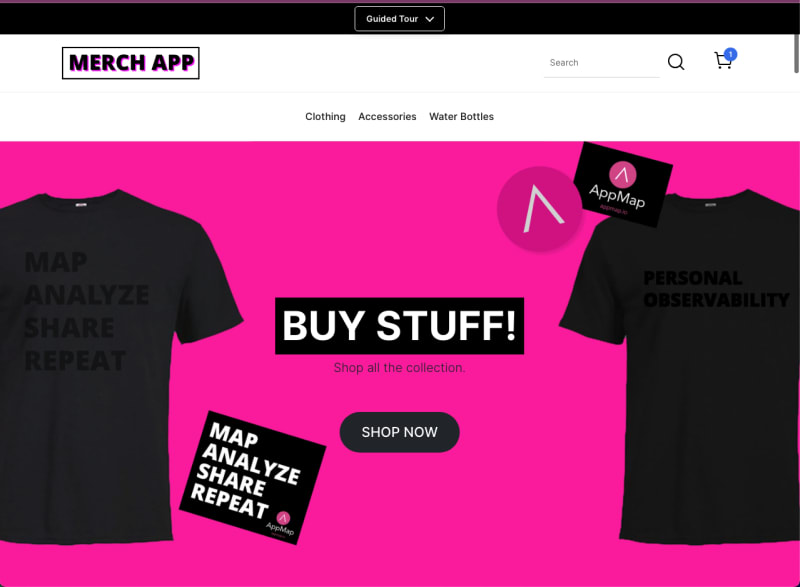
When looking at a sequence diagram of cart interaction you’ll notice that the authentication step is missing when accessing the cart functionality. Clicking on the cart with an item already added to it does not prompt the user to sign in.
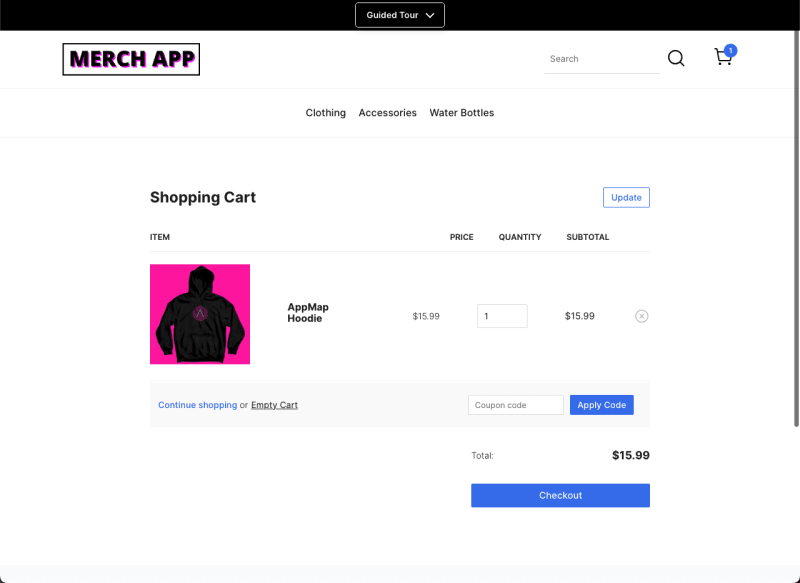
While this may be by design because the cart does not contain any personally identifiable information, the very next step in the purchase process does.
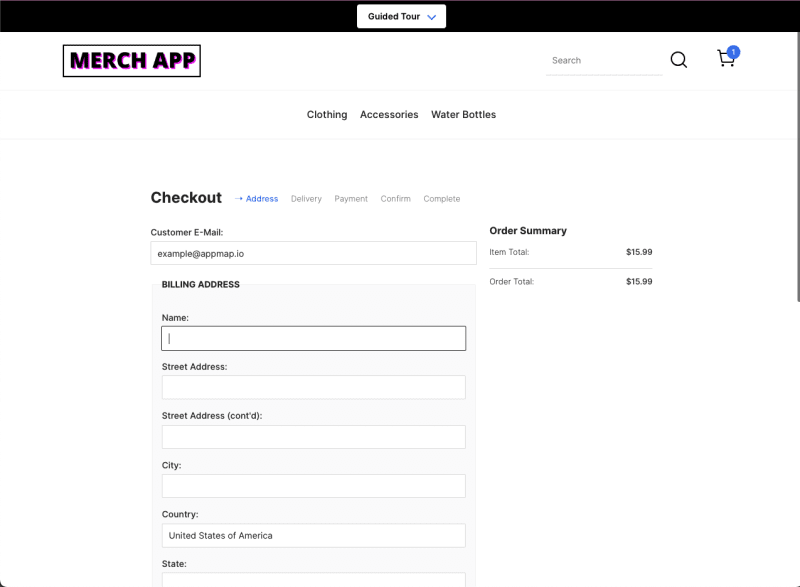
The application asks for a shipping address. In my opinion, a good rule of thumb is that any time we are capturing personally identifiable information once the information has been submitted the application should be authenticating that user. Any time that type of information is presented a user must be authenticated and authorized before viewing or updating.
AppMap: A Powerful Runtime Analysis Tool
It can be challenging and time-consuming to uncover and address these security concerns. Often times software teams look to tools or audits to provide us with a direction on what is causing the issue, which can be complex and require hours of investigation. The AppMap runtime analysis tool can give us a comprehensive look at the problem, what is causing it, and where it comes from in a matter of minutes. AppMap provides insights into how our applications behave at runtime, allowing us to analyze their execution flows and detect potential issues. With AppMap, we can identify and potentially fix security vulnerabilities, such as authorization-before-authentication problems.
Analyzing
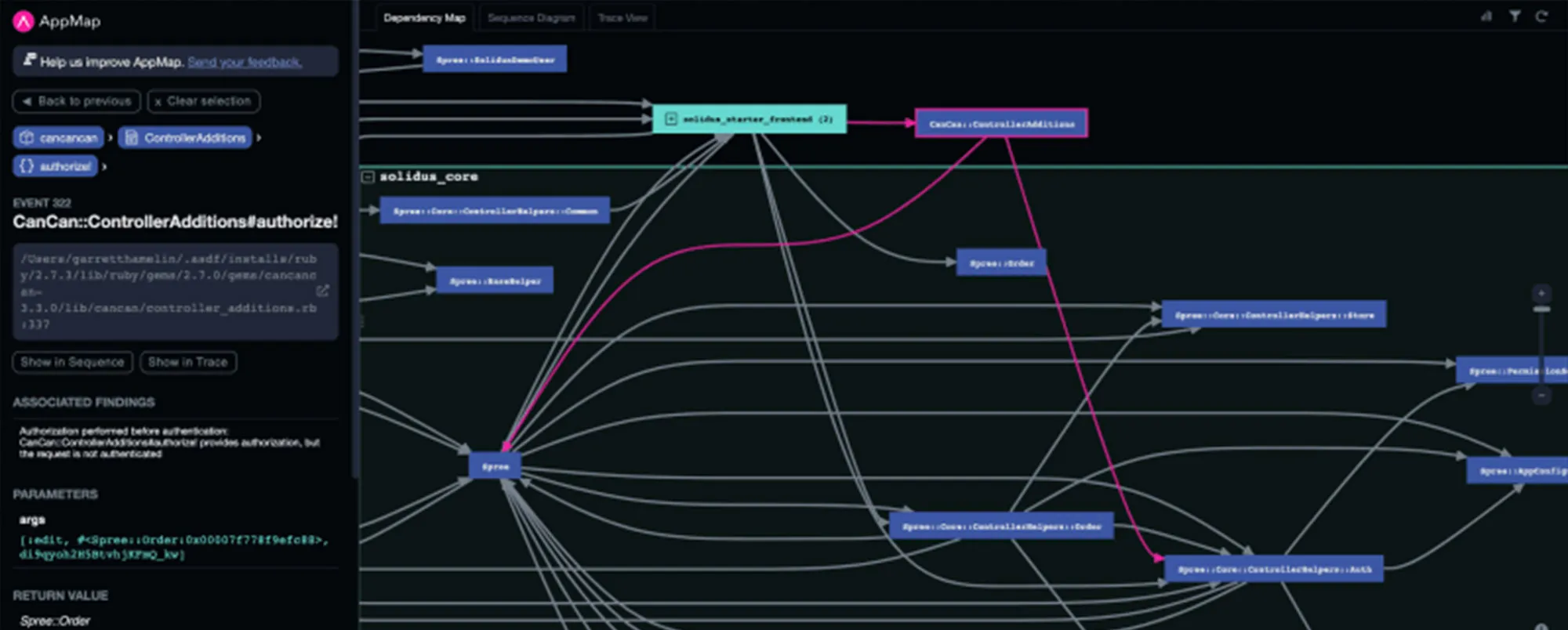
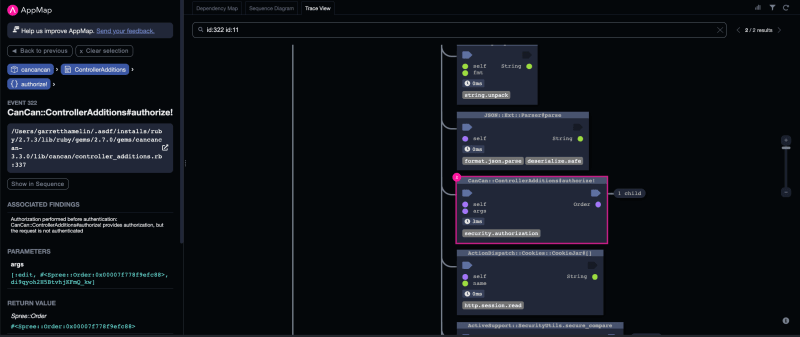
Analyzing the code using AppMap, we discover that the violation of authorization-before-authentication occurs in multiple instances within the application. Specifically, we observe the use of CanCan, a library for authorization, which performs authorization before any authentication check.
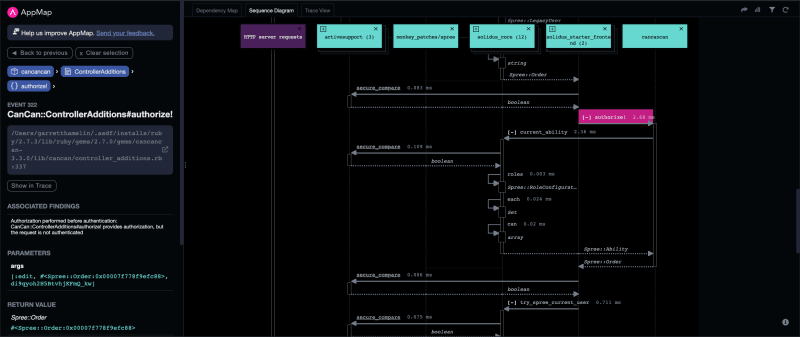
Inspecting the trace view and sequence diagram in AppMap, we trace the flow of events leading to the violation. We find that the “get cart” process triggers the authorization step without first authenticating the user. This type of behavior could allow unauthenticated users to access restricted resources.
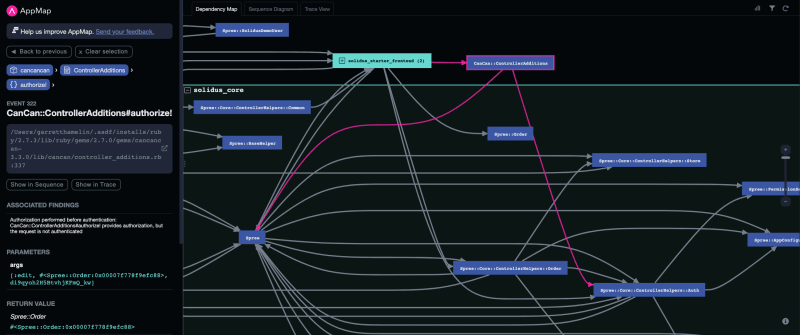
As we explore the dependency map, we notice that the authorization call is sent to the Spree Order controller, which resides outside of our application’s codebase. This presents a challenge since we lack direct control over Spree’s authentication process.
To address this security risk, we need to modify the order of operations and ensure that authentication occurs before authorization. In this specific case, the README of the application states that every request is assumed to come from an admin user, which is a major red flag. To mitigate this, we can implement the following strategies:
- Authenticate Before You Authorize: Flip the order of authentication and authorization, ensuring that users are authenticated before granting them access to restricted resources. In our case, we may want to know who a user is or perform a basic authentication before adding something to a cart on the off chance that a user would like to save that cart for later or to prevent abuse of the cart system for exclusive limited release items (I’m just spitballing here there are a ton of reasons it may be a good idea to establish a user identity before performing an action).
- Validate Credentials in Development Environments: Even in development or QA environments, enforce authentication to replicate real-world scenarios and identify potential vulnerabilities early on.
- Employ Anomaly Detection and Adaptive Access Control: Utilize artificial intelligence or machine learning techniques to create anomaly detection systems, threat protection mechanisms, and adaptive access control. This hybrid approach allows for flexibility in development environments while providing robust security controls in production.
By adopting these strategies, you can strengthen the security of your web APIs and prevent unauthorized access to sensitive resources. It is crucial to prioritize security throughout the development lifecycle to avoid compromising user data and maintain the trust of our users.
Summary
Authorization before authentication is a vital security principle that ensures users are properly identified and granted access to resources. By leveraging tools like AppMap and following best practices, we can proactively identify and address security vulnerabilities early on, ultimately building more secure and reliable web applications.
Thank you for joining me in this exploration of authorization before authentication in web API security. Stay tuned for more articles, and if you have any questions or suggestions, feel free to leave a comment in Slack!