See What's Important,
Not The Internals
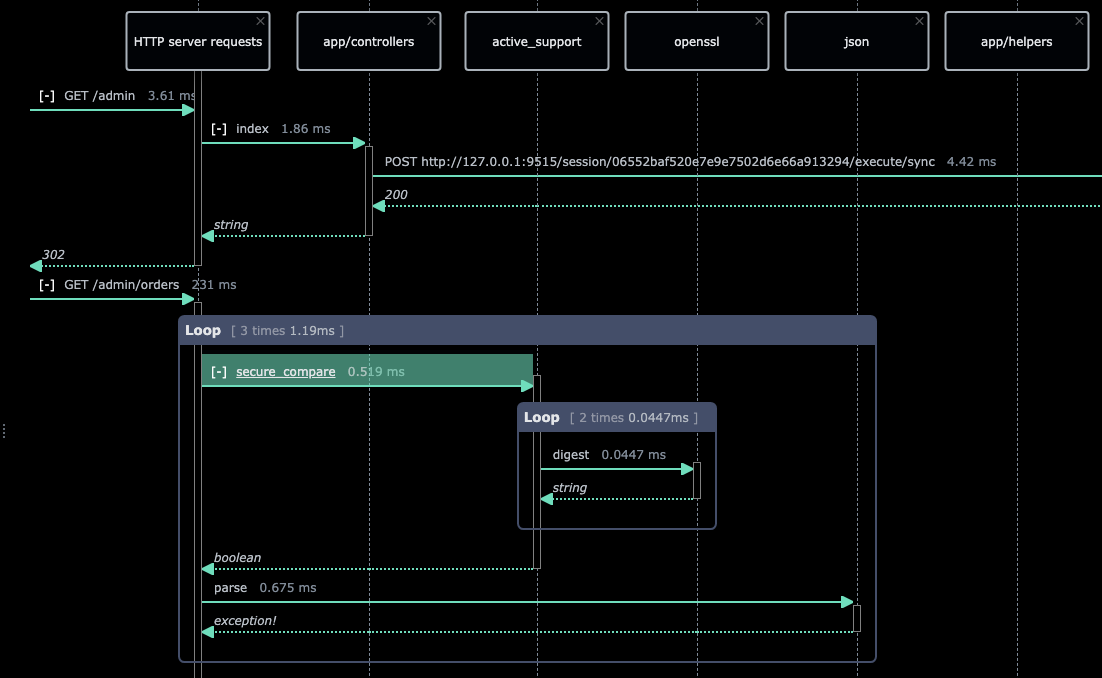
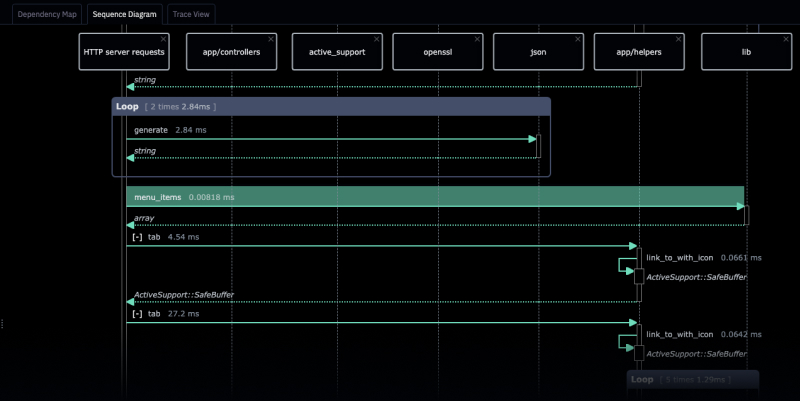
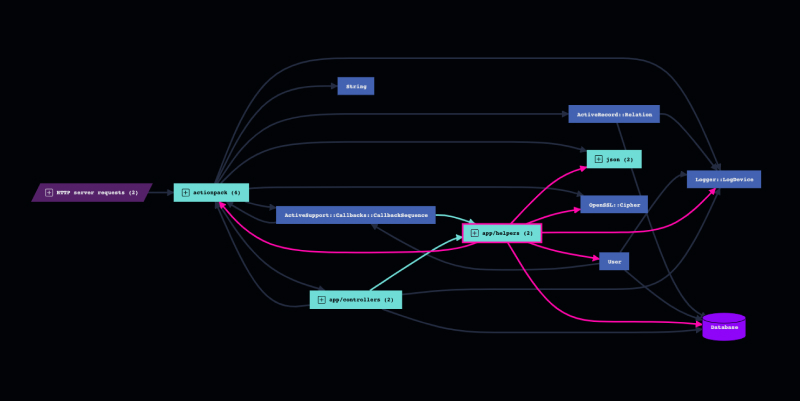
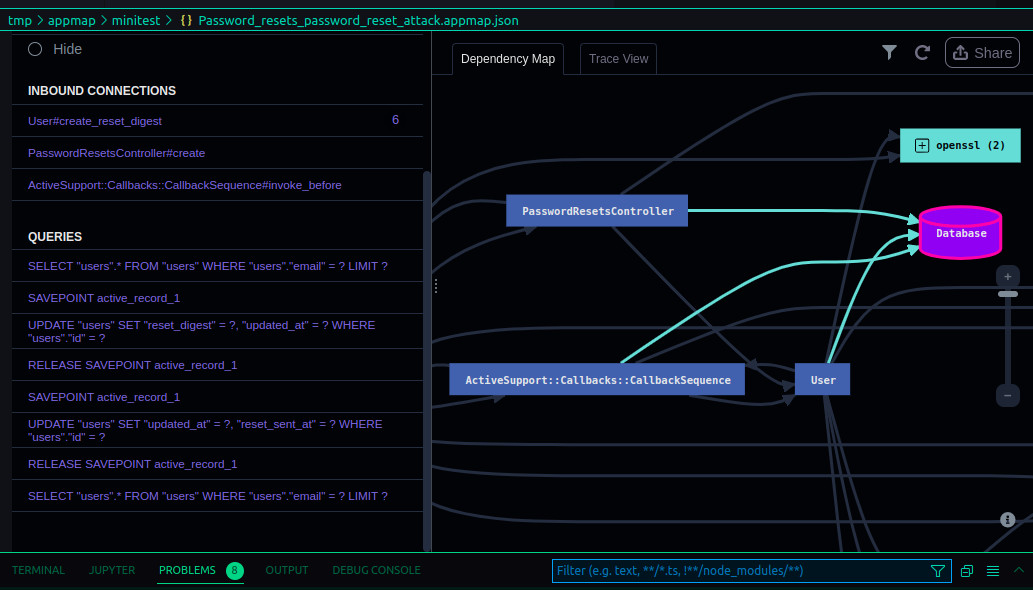
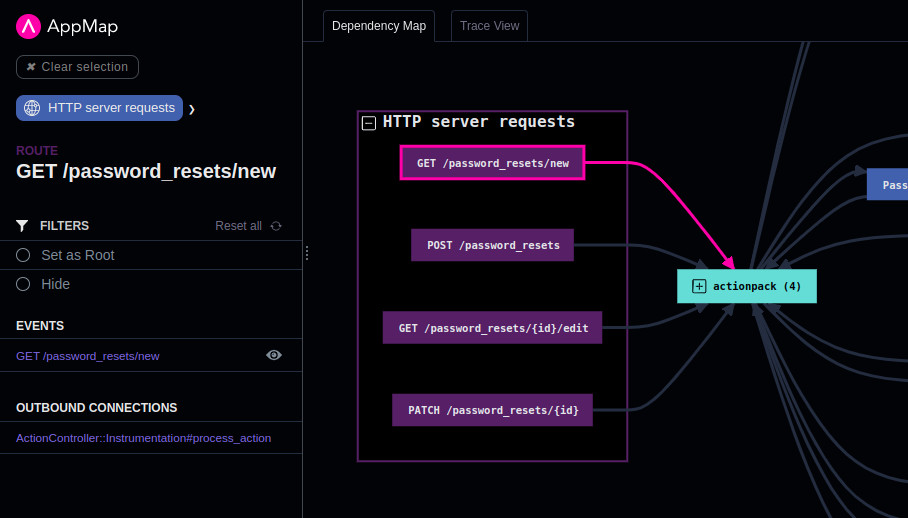
AppMap knows how popular frameworks like Spring, Rails, Django, and Express work. That means that when you view an AppMap, you'll only see the important parts of how an API request is handled.
For example, instead of seeing dozens of internal events related to how a framework receives data over TCP, manages its thread pools, and unmarshals payloads, you'll instead see something simple like HTTP POST.
Since it knows how these frameworks operate internally, AppMap will also automatically label framework function calls that provide important services. For example, AppMap will apply the crypto.decrypt label to an OpenSSL decryption function call, or the security.authentication label to any call to a function that validates a user's identity. Those labels then make it easy to understand, search, and analyze code execution paths.