Instant, Accurate Security Scans
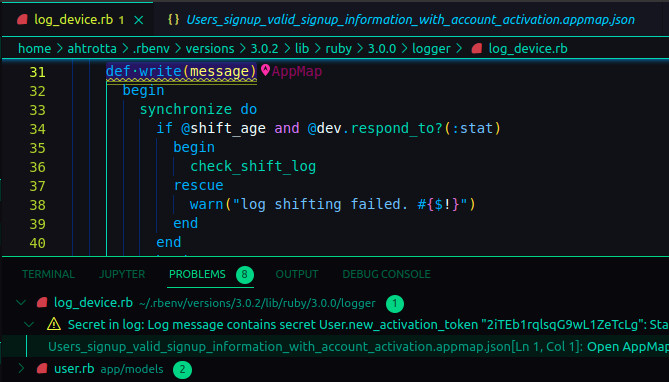
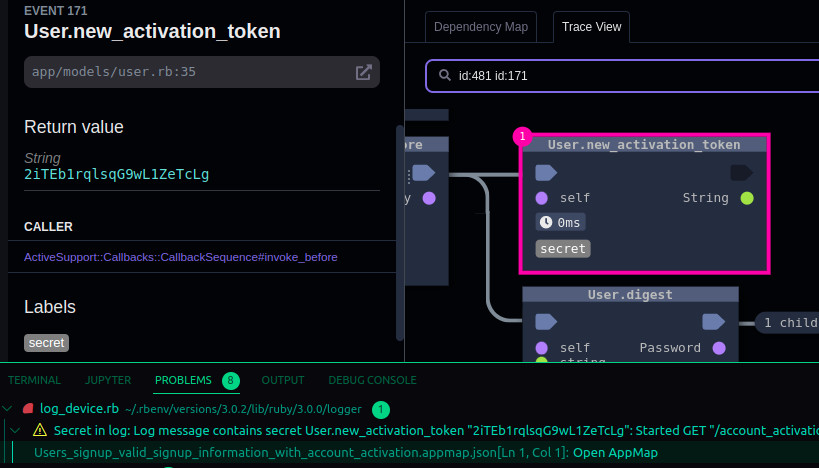
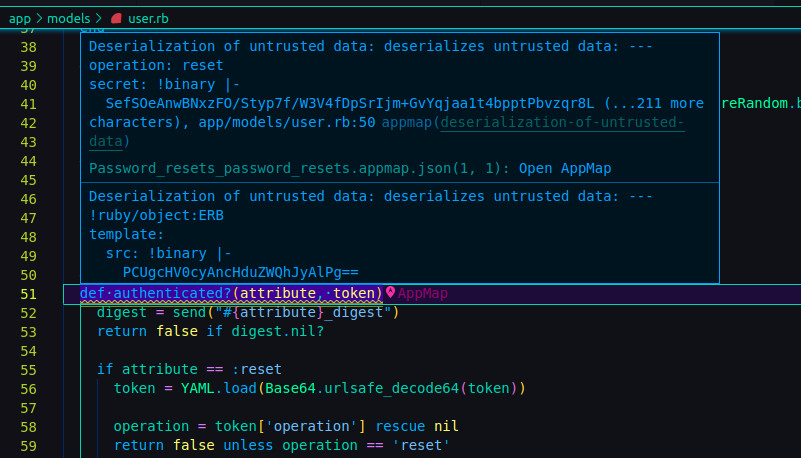
As soon as AppMap Data appears in your code editor, it is analyzed for security flaws. Any flaws found are highlighted in your editor almost immediately, linked to the appropriate places in the AppMap Diagram which show where the flaw exists. The source code containing the flaws is highlighted to make it extremely easy to find and fix the security problem.
AppMap Analysis is a next-generation security scanning product. Not only does it work much faster than traditional DAST and IAST tools, it is also able to be extremely definitive in its findings. Legacy tools might find an attack vector in your application, but they don't help you find the exact lines of code where the vulnerability exists. AppMap Analysis pinpoints the exact parts of your application - right down to the lines of code - that need addressing, and why.